Executive Summary
Today’s modern business has good reason to consider offering identity protection to its customers. Guarding against identity theft, fraud, and scams represents a pressing, widely felt consumer need that has grown vastly in extent and complexity over the past twenty years. The risk is illustrative of the endless information sharing, the always-on internet-connected devices that fill our homes, and the technologies that afford us conveniences in life that we could have never imagined before the 21st century. Indeed, the threat should not be left to the individual to battle on his or her own; it is the responsibility of all organizations to help their customers protect themselves.
The typical options available to businesses to offer protection have serious drawbacks, however. In particular, there is limited monitoring coverage and a rigid user experience that often does not align with how they do business. These shortcomings not only leave gaps in protection for consumers, but they also homogenize identity protection offerings, leaving little competitive advantage for the businesses who offer them and often producing solutions that don’t resonate with their audience
The modern state of the identity protection market demands a different mindset. Specifically, it has become clear that for identity protection to be effective (both for the consumer and for the business offering it), the customer experience must be uniquely tailored to the end user.
Iris® Powered by Generali has developed a new way for organizations to offer identity protection. Iris allows companies to make decisions about their program based specifically on their target audience and business preferences – so they’re not stuck with deciding between one under-utilized, cookie-cutter model or another and don’t feel limited geographically if their business strategy extends outside of the U.S.
The Dawn of In-Home Internet Access Brings More than Just a New Pastime
“Welcome. You’ve got mail!”
It’s a nostalgic phrase for most. These words would commence our time away from reality. Our time to disconnect, so to speak.
The truth was, however, we were connecting in more ways than we could ever conceive. And while connecting to the internet is benign on its own, bad actors quickly found ways to exploit it – as well as the programs, software, and applications that Americans grew to love, alongside their newfound internet access.
Twenty years ago, in 2004, federal regulators warned that the internet would become the thriving frontier for identity theft – even though 72% of personal information theft that year was committed offline1. Friends, family members, and neighbors accounted for half of all known thieves and cost victims a painful $15,607 on average2. It was a time when fraud spread and grew, undetected for long periods of time while victims were blissfully unaware.
Fast forward to 2024. Today, it’s hard to think of moments when we’re not online – unless maybe when we’re sleeping (but even then, our internet-connected phones are typically just an arm’s length away). And our homes no longer house just one shared family PC; instead, we keep a collection of many wi-fi-enabled smart devices. So, really, we’re never not online.
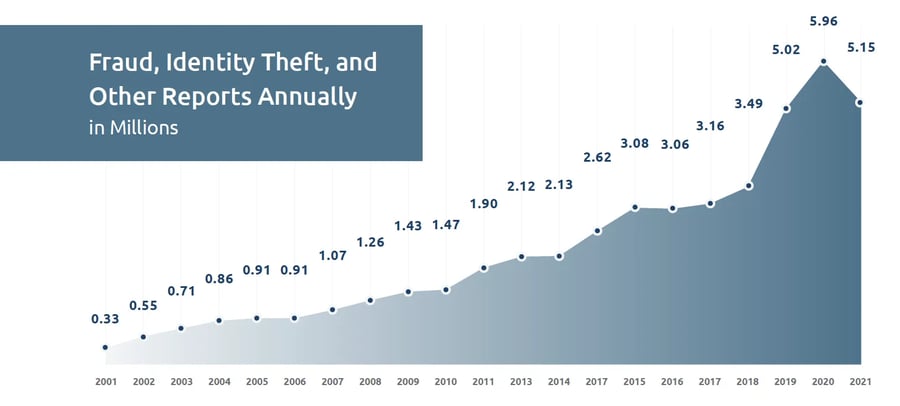
Where does that leave us? Well, federal regulators were correct twenty years ago when they predicted the internet would become an identity theft hot spot. If the below graph from the Federal Trade Commission’s (FTC) most recent Consumer Sentinel Network Data Book tells us anything, it’s that fraud and identity theft have been steadily increasing every year since the early 2000s, with few exceptions. Additionally, Consumer Affairs says that recorded instances of identity theft have soared by 584% over the last twenty years.
Ouch!
Early 2000s: Federal Regulations & Consumer Reinforcements
In 2003, the Fair and Accurate Credit Transactions Act (FACTA) was enacted to ensure that consumers have access to one free credit report a year, while also making companies and employers responsible for data leaks that led to identity theft. But checking your credit report once a year – or once every four months if you stagger them from each of the three credit bureaus, as we were all judiciously told to do – still leaves ample time for fraudsters to rack up a mountain of damage. And, let’s be honest, the vast majority of consumers weren’t, in fact, pulling their credit reports three times a year to check for fraud.
But even before free credit reports were federally mandated, there were a couple other recommendations drilled into consumers if they wanted to try to escape the looming threat of identity theft. They were told to stop carrying around their Social Security card in their wallets (remember those days?); to secure any bills, statements, or other paperwork with personal information in their homes; and to routinely review credit card and bank statements to ensure all purchases were legitimate.
Perhaps at the top though was to shred their sensitive mail and documents before tossing them in the trash. As a result, personal shredder sales skyrocketed: Fellowes Manufacturing Co., a leading manufacturer of in-home shredders, estimates that nearly 7.8 million of the devices were sold in 1999, up from only about 100,000 in 19903.
“The shredder gives people the feeling that they have regained some ground in a heretofore losing battle to keep their private information private.”
Outside of shredders, there weren’t many other purchases the vigilant and diligent consumer could make that would help to keep their information safe and out of the hands of thieves. And, as much as shredders were championed at the time, top security advocates admitted that they were likely only marginally beneficial.

Identity Theft Risk Means Opportunity for Some – But Not All
It didn’t take long for companies to jump on this growing opportunity: by 2005, a few companies began offering monitoring services. Essentially, technology was leveraged to scan for fraudulent accounts on credit reports and/or search for compromised data or credentials on the deep and dark web. Alerts were sent to customers when suspicious activity was found – and they could then stop the thieves in their tracks. Or that was the plan anyway.
But most victims had no idea what to do. Whether they were alerted to the fraudulent activity by their paid-for identity protection service, their bank, or they found it themselves, they were still left struggling to pick up the pieces on their own. For almost all victims, it was a deeply distressing experience.
(This is where we come in.)
In Washington, DC, there was a company (then Europ Assistance USA) handling emergent travel crises for other companies’ people all over the world. That was us!
You can imagine how stressful it would be if you were in a foreign country and something went terribly wrong (i.e., your wallet was pickpocketed, your passport was stolen, or God forbid, war broke out). These were the types of situations we dealt with day in and day out. Our customers truly needed support, empathy, and guidance – and that’s what we provided, literally turning their distress to relief.
Our story began as pioneers in the assistance industry back in the 80s, with “care” engrained in our DNA from our French parent company, Europ Assistance. Following their mission statement (which is still ours today), we brought people “from distress to relief – anytime, anywhere.” While some companies’ mission statements are more aspirational or elusive, ours is something we execute on every day; it’s tangible and impactful. It’s also what took us on our path into the identity protection world.
Iris CEO, Paige Schaffer, who has led our identity protection business since its early days, says, “We were an organization built on helping people, and we became keenly aware of a gaping hole in America’s identity theft landscape. Victims had no one to turn to, and the very businesses that should have been helping them were treating them as if they were the ones who perpetrated a crime. We felt strongly that we could take our skillset and channel it into a new business that could undo the damage that fraud victims were dealing with and help them get their life back.”
By 2004, we were taking our first identity theft resolution calls. Because we were one of the very first companies to offer such a service, we had no framework to follow. We became resolution experts by researching and documenting, and then by handling each new and sometimes complicated case as they came in (and then documenting some more). We contacted credit bureaus, banks, law enforcement – essentially any entity necessary to restore our customers’ names and prevent further damage – while doing it with the white-glove, empathetic care we were founded on. The space has evolved tremendously since then, and we’ve been sure to stay at the forefront, with our resolution specialists boasting the following accreditations today: Fair Credit Reporting Act (FCRA)-Certified, Certified Identity Theft Protection Advisor (CIPA), Certified Identity Theft Risk Management Specialists (CITRMS), and CompTIA Security+.
Of course, it didn’t take long for other identity protection providers to catch on. Resolution services were clearly essential to providing a robust protection plan, and today you’d be hard-pressed to find one without them.
"We felt strongly that we could take our skillset and channel it into a new business that could undo the damage that fraud victims were dealing with and help them get their life back."
The Identity Protection Market & Today’s Consumer
So, while the penetration of identity protection products in the American home has come a long way over the last two decades, there’s still a wide gap.
It’s a gap that’s shifted in an interesting way – and not steadily shrinking as one would assume. Instead, identity protection has become increasingly fragmented as the space has evolved. Yes, awareness levels of identity protection have grown exponentially, but identity protection no longer seems to be viewed through a holistic lens. We see instances of partial identity protection offerings embedded in adjacent or security-related products, but there’s even an entire mini-industry dedicated to them. Consumers that are repeatedly exposed to fragmentary protection options are invariably led to believe that these solutions will deliver the protection they need. It’s the sum of these parts, however, that provides the best protection to one’s identity.
Further adding to the misperception of protection is what we’ll call “the data breach apology package.” We’ve seen scores of data breaches inflicted upon consumers over the years – some of which have profoundly rocked customer confidence. In an attempt to recoup customer trust (selfishly or not) or their hand was forced by law, organizations routinely offer watered-down or difficult-to-access identity protection – primarily monitoring and resolution services – to those victimized for a pre-determined amount of time.

Unfortunately, exposed data doesn’t present risk for a fixed amount of time; it will always pose a risk. In fact, one could argue that the longer that it’s been exposed, the riskier it becomes as it’s likely being compounded with other pieces of compromised data from various breaches over time. With so many breaches affecting so many individuals, we now live in a society where the average person may have a couple overlapping “identity protection” solution sets. However, this isn’t as ideal as it may sound, which we’ll soon see.
On the other end of the spectrum, you have the packages you pay for on an annual or monthly basis for yourself or your family. These packages typically come in three tiers – good, better, best – and offer a set of tools available via a dashboard. How much engagement they get is dependent upon the type of user, but since the service is being voluntarily paid for, it likely sees higher utilization than the other types of solutions mentioned.
The result is a curious hodgepodge that is still leaving vast swathes of consumers under protected or altogether unprotected – not overprotected as the described circumstances may appear.
Why? Various free and embedded protection pieces are well-intended, but the recipient sometimes walks away with a false sense of security. A false sense of security may be more dangerous than the un-monitored consumer – with those that feel “protected” perhaps engaging in riskier behavior.
It is these already-exposed individuals that, as you might guess, don’t have the level of protection they’d like to believe. These types of freebie monitoring tools and services often come with cutoff dates and limitations, and they’re not utilized the way strategic, customer-centric programs are.
The identity protection market has become so commoditized that robust, engaging identity protection programs have taken a back seat. And sadly, that’s exactly what’s been needed to help close the gap.
So before we hone in what it might take to bridge the divide, it’s important to examine what an ideal (and realistic) solution would look like from the consumer’s perspective.
A Note About The Space
Over the last decade, we’ve seen a profusion of mergers and acquisitions, leaving increasingly less competition amongst identity protection providers.
According to good, old economics, a lack of competition will chip away at the buyer’s power and likely only bring rising costs to the end user or, in some cases, the re-seller/provider. The identity protection market is unique in that taking away the buyer’s power only undermines the market’s value – assuming the goal is to provide protection to as many consumers as possible.
More importantly though, less identity protection solution providers will also give way to less variation in identity protection offerings. When identity protection all starts to feel the same, client organizations are left with cookie-cutter feature sets that don’t necessarily line up with their business’ goals or are irrelevant to their audience. It’s also likely that user enrollment options are limited, resulting in a process that feels unfamiliar to their customers (and leading to less activations). Additionally, we’ve seen insufficient branding capabilities that yield environments that often feel foreign to the end user. So even if they do activate their identity protection program, it’ll be less likely that they’ll continue engaging with it in a way that will bolster their identity security.
The Consumer’s Perspective
Certainly, while we know that everyone is at risk for identity theft and fraud, not everyone perceives that risk the same way. Some of us are more prone to worrying about the “what ifs” in life, and others prefer to not stress about something they believe is largely out of their control. And then there are many people who fall somewhere in between.
This perception of risk, coupled with an individual’s financial resources and their understood accessibility as a consumer, are often some of the primary factors that determine whether they are utilizing an identity protection program or not. Outside of education and awareness (both important and worthwhile endeavors!), changing a person’s perception of risk isn’t always practical. We also can’t change how much flexibility consumers have in spending money on something that, to date, is still viewed as a “nice to have.” That leaves the consumer’s accessibility. And therein lies our answer. The ideal identity protection solution is highly consumer-accessible.
We note that accessibly is a word that can be interpreted multiple ways, but for the purposes of this discussion, we use it to mean that identity protection would integrate easily into one’s current lifestyle; it wouldn’t feel like another account to manage; it would be an extension of a digital place that they already spend time in. Equally important, identity protection is a highly personal matter, so consumers are more likely to be receptive to an identity protection program made for them, by an organization they already trust and do business with. Familiarity, simplicity, and personalization matters – a lot.
A New Way to Offer Identity Protection
Twenty years ago, we saw a void in the identity theft protection space. Consumers’ needs weren’t being met, and although we had never resolved identity theft cases at that point in time, it felt like a natural (and necessary) thing for us to do. And while we continue to offer 24/7/365 white-glove resolution assistance, we also offer over a dozen other identity protection solutions that run the entire gamut.
Today, we’re again filling a void – because consumers’ needs aren’t being met the way that they should be. So much has happened in the last two decades, and yet the identity protection market seems to have evolved in a way that is mostly advantageous for the businesses providing the services – not for the very people that the market was created for. At Iris Powered by Generali, that’s not why we do what we do.
So, we’re leveraging our business-to-business-to-customer (B2B2C) model to give businesses a new way to offer identity protection: it’s the Iris identity protection platform. At Iris, we don’t presume to know what would make identity protection the most accessible for our clients’ customers; that’s their expertise. They know their customers’ lifestyles, habits, and preferences best. And they also know their businesses best.
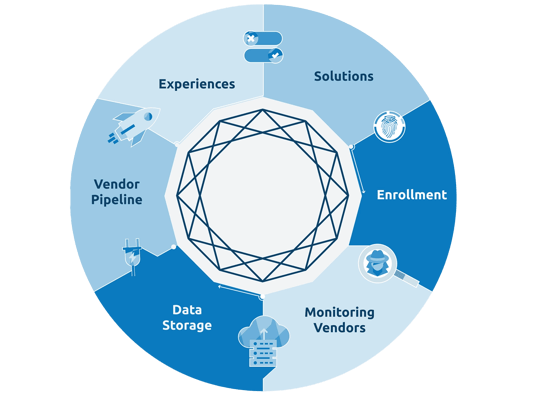
With the Iris identity protection platform, our partners can build their program from the ground up. From choosing how their customers access the tools and what their experience and interface looks like, to what solutions make the most sense for them and which monitoring vendors they want to use – Iris identity protection is now the most personalized and consumer-accessible solution available.
The B2B Identity Protection Check List
Businesses that want to offer identity protection alongside their existing products or services would benefit most from a solution that is highly flexible – not an out-of-the-box, templated one meant for a very limited user base.
Above all, flexibility of the interface is crucial. This is especially true for companies with their own software development capacity to leverage features fully embedded within their own environments. Outside of this though, consumers want identity protection that feels familiar. Not only will this encourage usage, but it will also have a positive impact on their own brand. Worth mentioning, too, is that there are companies with audiences that want a separate, dedicated portal, so there should be ample room for both options.
Secondly, companies should look for flexibility in the features and services that they decide to offer their customers. Being able to craft exactly the right mixture of active monitoring, live resolution, and educational features that appeals to their target audience will mean that the solution will see higher utilization. Depending on your industry, you could also want to put out a distinctive, more vividly differentiating solution.
Businesses should also consider consumer journey engagement tools. Every individual has their own feelings about the need and value of identity protection, and some may even have a bit of trust issues. Having the option to offer smaller features as a “taste” or “teaser” of identity protection – an introduction of sorts – that can help encourage customer adoption can be helpful to their program’s success.
Without this kind of flexibility, businesses will miss out on successfully acquiring and retaining customers in their target market who otherwise would exhibit strong demand to be better protected against identity theft, fraud, and scams.
Identity Protection Made for Your Business & Your Customers
By offering your customers a solution tailored to their needs in an environment they already go to or want to spend time in, you can bring identity protection into homes in a truly meaningful way – that is, one that will help close the gap.
Think about how your customers typically access and use your product or services. How can you meet your customers where they already are? Imagine if identity protection tools were integrated into your own digital experience or if they could seamlessly navigate from that environment to one dedicated to their identity protection tools.
At Iris, we’ll set up access to your identity protection services to match your business or membership model – whether that means customers connect through your existing system via SSO, supply a member ID or promo code, get enrolled via API or recurring list uploads, or something else. This ensures that your customer journey feels authentically yours.
We’ve seen, from experience, that this will have a greater impact on customers’ identity security. In the past, B2B2C identity protection offerings provided customers with portal access via a separate username and password. While this setup seems totally harmless and respectable, your customers may needlessly get turned away from adopting the well-intended program. And you can’t blame them; if it’s not part of their everyday regimen or they don’t even recognize that your company is providing it, it can be easy to forget about.
Additionally, you can choose whether the solutions you choose to offer your customers are accessible via a web portal in your branding, directly through your app or website via API integration*, or as a single branded feature if you want to focus on a specific risk type. Whichever you choose, it will all feel like an effortless extension of your brand.
We also let you decide things like which and how many monitoring vendors you want to use. For some partners, this may be a minor detail or way too detailed for them to determine; but for others, having this decision-making capability is an important piece to building the ideal identity protection program for both their business and users. The Iris platform plugs into an evolving base of monitoring and cybersecurity data partners, so that you can provide your customers all-encompassing identity protection coverage. We’ll aggregate and normalize data from numerous sources and develop secure integrations with specific partner organizations.
And, of significance, you can even choose if you want to hold customer data or have it transferred directly to us. We’re always listening to our partners’ concerns, and some clients are unsurprisingly wary of taking on the new risk that holding sensitive data (that they wouldn’t otherwise be collecting) would present. With Iris, our partners don’t have to make that sacrifice to offer powerful protection to their customers.
Lastly, our flexibility also extends geographically. In fact, we love when partners come to us with a global identity protection strategy. No one knows better than us that identity protection looks different around the world. We’re fast and furiously bringing identity protection solutions into new markets – over 112 countries and counting! – and it’s just one more way we’re shifting the identity protection space.
It’s a Full Circle Moment
Iris CTO, Erik Nienaber, put it like this:
“Our specialty is to find ways that we can directly support our clients’ mission as it relates to identity theft. A good part of our success has been to lean in closely when it comes to interacting with our clients, defining what identity theft means for them, and listening to their problems and challenges so that we can surface the appropriate solution for them. We do this in a bespoke and custom manner, ensuring that our technology delivers on the goals they’re trying to meet, and all Iris tools are crafted in a way that works for their business and customers.
The challenge ahead of us is that clients not only want greater access to a wide range of identity theft services, but they also want many of the more tedious day-to-day tasks required to support an identity theft product line to be streamlined. We’re constantly looking for ways to minimize the risk associated with the handling of sensitive information and investigating alternatives to requiring them to share personal data across parties.
Our partnerships have also taught us that there’s a need for more detailed insights into how their product and end users are doing. Clients want that data to help them evaluate the efficacy of the services they’ve selected – and to make adjustments on the platform quickly if they are not valued by their users. We feel strongly that we’ve got something pretty novel here, and it will go a long way in making identity protection more usable.”
But ultimately, it’s our partners and their customers that will say for sure. As an identity protection company rooted in care that’s always found themselves moving beyond the status quo, Iris is simply doing what we can to help them – and we’re confident this is the best way forward.
Twenty years ago, when identity theft resolution services were infrequently offered, we were happy when other organizations followed in our footsteps; it meant more people could receive such an essential service. And we have the same hope for society now. If other companies join us in taking this new approach to offering identity protection services, we know that more people will have personalized robust protection. And that may just be the only way to close the gap and bring those rising fraud numbers down – for maybe the first time in twenty years.
"A good part of our success has been to lean in closely when it comes to interacting with our clients, defining what identity theft means for them, and listening to their problems and challenges so that we can surface the appropriate solution for them."
Iris® Powered by Generali is a B2B2C global identity and cyber protection company owned by the 190-year-old multinational insurance company, Generali. We opened our first Washington, DC office in 1982 with a simple mission, bringing customers from distress to relief – anytime, anywhere – and went on to become one of the very first identity theft resolution providers in the U.S. in 2004.
Today, our offering combines always-available identity resolution experts (real people, 24/7/365) and tech-forward solutions that uncomplicate the protection process.


.png?width=102&height=102&name=Iris-Generali-Logo-White%20(1).png)




