Estimated Reading Time: 3 Minutes
One of the many valuable features of Generali Global Assistance (GGA) advanced identity monitoring offers is the continuous scouring of the deepest and darkest corners of the Internet, on behalf of our customers, to search for any compromised credentials and potentially damaging use of personal information. However, a common question our clients and customers ask when we mention this feature to them is – what exactly is the deep, dark web?
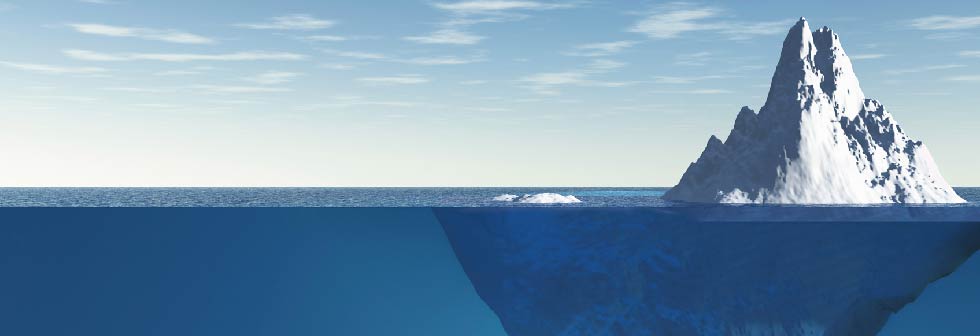
To understand the deep, dark web, one must first understand that, while the two are related, the deep web and the dark web are not one in the same. The deep web is the dynamically populated aggregate of unindexed websites (websites that cannot be found in traditional search engines like Google), including dark webpages, and is accessible only by querying a search box on a deep website. In other words, the deep web can only be accessed by conducting a search that is within a particular website.
The dark web is any webpage people can visit without third parties being able to trace the location of the web visitors or the webpage publisher. Usually, sites on the dark web are protected by encryption technologies but sometimes they’re protected merely with password-protected forums. The dark web is accessible via special browsers such as TOR.
The key takeaway here is that the dark web is part of the deep web.
The deep web sounds sinister, but much of it is quite boring. Some examples of more mainstream websites with webpages on the deep web are bank account sites, registration-required web forums and much of Facebook. The deep web is said to comprise about 90% of the Internet. However, included in that 90% is the dark web, which is much smaller, comprising less than .01% of the Internet.

The dark web, on the other hand, is where one can find more of the insidious webpages typically associated with the terms “deep, dark web” — for this reason it is frequently referred to as the Internet’s “underground.” One of the most famous dark websites was Silk Road, which was essentially a criminal version of eBay that was shut down by the FBI twice, both in 2013 and 2014. All illegal items and services purchased on Silk Road, from credit card numbers to hitmen, were done using Bitcoin (a common currency used in the black market) making all transactions completely untraceable. It’s on illicit dark websites like these that our monitoring typically searches for and finds compromised credentials and attempted use of stolen personally identifiable information.
Our advanced monitoring solutions include identity monitoring that uses proprietary technology and skilled personnel to continuously scan the deep and dark web to find current and potential threats that our customers need to be made aware of.
In particular, our monitoring solutions include:
- Internet surveillance – proactively comparing customers’ personally identifiable information and the data they enter into their monitoring dashboard to data that has been compromised
- Compromised credentials – scanning for customers’ exposed login information that is linked to malicious breaches and underground infiltration
Not only are our monitoring solutions’ technology advanced, they’re also very user-friendly. In one recent example, our monitoring solutions found some customers’ comprised credentials for their LinkedIn and Twitter accounts on the dark web. We alerted these customers via email as well as in their online dashboards providing next steps for them to take, including the option to speak with one of our award-winning customer service team members. These monitoring solutions allow our customers to live their lives worry-free, resting assured that our monitoring and team is working and available 24/7 to ensure that their personal information stays personal. To learn more request a demo today.


.png?width=102&height=102&name=Iris-Generali-Logo-White%20(1).png)




